FAKE NEWS. THE NEW DIGITAL ATTACK
AUTHORS: ANDREA MELISSA DE LA O SALAZAR, EDGAR JAVIER PALACIOS ZAMORA, LUIS EDUARDO PINEDA DÍAZ
TRANSLATED INTO ENGLISH BY MARTA ÁLVAREZ COLLADO
The term "Fake News" can be something new these days or something very well known by some; basically "Fake News" fake news are false pieces of information whose main purpose is deception or defamation and are generally economic or political in nature. Apart from this, they have the characteristic of being quickly distributed through several mass media: as, for example, social networks. This is what makes them be such an important medium for digital attacks nowadays.
Let’s remember that the term "Fake News" refers to untrue information and, as its name suggests, it is misleading information that is disguised as legitimate news.
According to a study carried out by the computer security company Kaspersky (Kaspersky, 2022), these fake news can be classified into two large categories:
- Stories deliberately imprecise: that is, people know that they are fake stories but they are published anyway. They may do this to manipulate public opinion or to redirect the traffic to a specific website.
- Stories that contain real elements, but that are mostly imprecise. This may occur because the writer has not checked all the facts or has exaggerated certain aspects to raise a particular point.
The so-called ‘hackers’, or social engineers, use "Fake News" quite often with topics that call the attention so that the inexperienced user lowers their guard, clicks on it, and infects their social media, or in more extreme cases, their computers, phones, or laptops, hence leading to the loss of important information or the impersonation of the individual to obtain access to their bank accounts.
TERMINOLOGY ON DIGITAL ATTACKS
Now that we know some important features about fake news, it is important to also know a bit about ‘malwares’ malwaresThese, according to the Malwarebytes webpage (Malwarebytes, 2019), are known as “malicious programs” and this is a broad term that refers to any program or malicious code that is harmful for systems.
El malware Hostile, intrusive, and intentionally unpleasant malware attempts to invade, damage, or disable computers, computer systems, networks, and mobile devices; often, assuming partial control of the operations of a device. Just like the flu, it interferes with normal functioning.
The intention malware is to illicitly extort money from the user. Although the malicious program cannot harm the hardware from the systems or the network —with a few exceptions— it can steal, encrypt, or delete its data, alter, or hijack basic functions from the computer and spy on the computer activity without your knowledge or permission
We should also recognize the most popular ones regarding their dishonesty and common use. According to Malwarebytes (Malwarebytes, 2019), these are some of the most common ones and they are recognized for their features:
- El adware • The ‘adware’ is an unwanted software designed to show advertisements on your screen, usually in a browser. It tends to use a surreptitious method: it pretends to be legitimate, or it attaches itself to another program to trick the user and get installed on their PC, tablet, or mobile device.
- El spyware is malware which observes the activity from the user on the computer secretly and without permission, and passes the information to the author of the software.
- A virus is a malicious program that is attached to another program and, when executed —usually without the user’s knowledge—, it replicates itself by modifying other programs from the computer and infects them with its own code bits.
- ‘Worms’ are a type of malware similar to viruses, which replicates itself with the purpose of being spread to other computers on a network, usually causing damage and destroying data and files.
- A ‘Trojan’, or Trojan horse, is one of the most dangerous types of malware. Typically, it is presented as something useful to trick the user. Once it is on the system, the attackers behind the Trojan get unauthorized access to the infected computer. From there, Trojans can be used to steal financial information or install threats such as viruses.
- El ransomware • ‘Ransomware’ is a type of malware that blocks the user’s access to the device or encrypts their files and then forces them to pay a ransom to return them. Ransomware has been recognized as the preferred weapon for cybercriminals because it demands a quick and profitable payment in hard-to-track cryptocurrency. The code behind the ransomware is easy to obtain through illegal online marketplaces but defending ourselves against it becomes very difficult
- El rootkit • ‘Rootkit’ is a type of malware which gives the attacker administrator privileges on the affected system. Usually, it is also designed so that it remains hidden from the user, from other system software, and from the operating system itself.
- A ‘keylogger’ is malware that records all user keystrokes, stores the collected information, and sends it to the attacker, who looks for confidential information such as usernames, passwords, or credit card details.
- Malicious cryptocurrency mining, also known as random mining cryptojacking, is a malware is an increasingly prevalent malware installed by a Trojan. It allows other people to use your computer to mine cryptocurrencies like bitcoin or monero. Cryptocurrency mining malware uses the resources from your computer but sends the obtained coins to their own accounts, and not to the account of the owner of the computer. To keep it short, a cryptocurrency mining malware steals your resources to make money.
- Los exploits are a type of malware that takes advantage of bugs and vulnerabilities in a system so that the creator of the exploit can take control. The exploits are linked, among other threats, to malvertising, which attacks through a legitimate website that inadvertently downloads malicious content from a dangerous site. Later, the harmful content tries to install itself on the computer after an involuntary download. With no need to even click. All you have to do is visit a good website on the wrong day.
Many people receive messages that are immediately sent to a large number of people, without having knowledge of sending the messages. This may contain a computer virus that attacks the devices which receive it, or there can be misleading messages with false content. These messages are known as hoax hoax’ (Panda Security, s. f.). The hoax The hoax covers various topics: health, computer warnings, stories, etc. They are designed to call the user’s attention by using them as baits. In some cases, it is not possible to tell if you are facing a hoax.
REAL CASES OF FAKE NEWS AND DIGITAL ATTACKS
1. Flight 370 from Malaysia Airlines
One of the biggest events that shocked the world in 2014 was the disappearance of flight 370 from Malaysia Airlines. As if the event by itself was not unfortunate enough, hackers and cybercriminals used the disappearance of that flight to send emails with false information, and they were infected.
These people knew that, since it was important information ─being it an event of global interest─, many people would open the emails because of the striking news. What would happen if you did? The system would be infected by a Trojan.
2. The WannaCry Attack
During May 2017, there was a global cyberattack which consisted of encrypting all the data from a computer, whether personal or from a company. To recover the data, the user was obliged to pay a “ransom” for them. According to the computer security company Avast (2020), the 2017 attack affected more than 230 thousand computers in 150 countries during the first day, many of them belonging to government institutions and hospitals.
This attack provoked panic among the users that were affected, with the uncertainty of being able to recover their information after making the payment. The institutions, on their part, saw how their databases were encrypted, forcing them to stop their services. Those responsible for this attack also took advantage of the innocence of the users, who did not know the nature of this threat and how to answer to it:
WannaCry is an example of encryption ransomware, a type of malicious software (malware) that cybercriminals use in order to force a user to pay. The ransomware attacks by encrypting valuable files so that you cannot access to them, or by blocking your access to the computer so that you cannot use it. (Kaspersky, s. f.)
The 2017 attack affected only the computers that used Windows as their operating system, this happening due to a security breach in that system. “The cybercriminals responsible for the attack took advantage of a weakness in the Microsoft Windows operating system through an attack that was allegedly developed by the United States National Security Agency” (Kaspersky, s. f.). Finally, the security breach was closed, leaving great financial and information losses, and being a type of attack that still exists today.
3. The "Fake News" AND POWER: THE SALVADORAN CASE
On June 1, 2019, Nayib Bukele took power as the President of the Republic of El Salvador. His victory at the polls marked the end of 30 years of bipartisanship in El Salvador. To date, one aspect of Bukele's presidency to highlight has been the use of social networks, both by him and by other members of the government.
The preferred social network by the leader is Twitterplatform that he uses to give announcements to the Nation, express his opinion about some topics or even give “orders” to his council of ministers (figure 1).
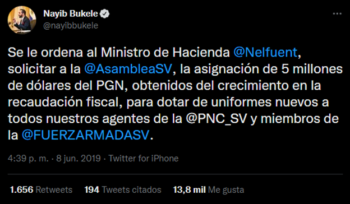
Being social media the place where the highest number of fake news appear and, given the high use of one of these by the leader, it is valid to question if all the posts from President Nayib Bukele on this platform are reliable or if, on the contrary, he has spread or created fake news.
The Communication Observatory of the Participatory Radio Broadcasting Association of El Salvador (ARPAS in Spanish) carried out an investigation to determine the veracity of the Salvadoran president's social media posts:
The Communication Observatory of the ARPAS (..) collected a total of five posts with misinformation generated from President Bukele’s Twitter account; and, for this, it was taken as a criterion to monitor for a period of one month the account of the Leader. (ARPAS, 2020)
The investigation concludes that Bukele has spread fake news more than once, and in some even denying the official authorities of other countries or of private companies:
The analysis of these 5 cases of disinformation content that come from an official source, precisely from the President of El Salvador, Nayib Bukele, confirms the alarming fact that a President replicates such content, which can be inferred as a strategy to keep his followers in a focus of attention that does not necessarily correspond to the Salvadoran reality. (ARPAS, 2020)
The fact that a person with a high political command, and with great popularity in social networks, (Bukele has around 4 million of followers on Twitter), is part of this “dynamic” of fake news, is of great concern, because his power and popularity make people believe that what he posts is completely true, without having the need of checking it out. Therefore, due to the behavior of these personalities, it is more necessary to verify sources regardless of who the information comes from.
CONCLUSION
The current context of a globalized and closely connected world through the Internet obliges its users to participate responsibly in its main means of communication: the social networks. To achieve this, it is necessary to know the risks and threats that hang around these platforms, in order to cope with them, avoid them, and denounce them with the available tools.
The responsible use of social networks is not only for individual benefit, but also for collective benefit, where people are informed about new trends in computer attacks and fake news to, together, fight against these dynamics on the network.
To conclude, it must be remembered that power does not legitimize fake news and the verification process is crucial before suspicious publications, coming from any person, even from a public official. The participation of these officials in this type of social network practices should be condemned, since they do not promote the values by which society is governed and their consequences weaken the construction of a culture of peace.
REFERENCES
ARPAS. (2020, 14 de abril). Las “Fake News” del Presidente Bukele. ARPAS. https://arpas.org.sv/2020/04/las-fake-news-del-presidente-bukele/
Bukele, N. [@nayibbukele]. (2019, 8 de junio). Se le ordena al Ministro de Hacienda @Nelfuent, solicitar a la @AsambleaSV, la asignación de 5 millones de dólares. [tuit]. Twitter. https://twitter.com/nayibbukele/status/1137489312067588097
Kaspersky. (2022, 20 de abril). Cómo identificar noticias falsas. latam.kaspersky.com. https://latam.kaspersky.com/resource-center/preemptive-safety/how-to-identify-fake-news
Kaspersky. (s. f.). ¿Qué es el ransomware WannaCry?. Kaspersky. Consultado el 9 de mayo de 2022. https://www.kaspersky.es/resource-center/threats/ransomware-wannacry
Latto, N. (2020, 27 de febrero). ¿Qué es WannaCry?. Avast. Consultado el 9 de mayo de 2022. https://www.avast.com/es-es/c-wannacry
Malwarebytes. (2019, 8 de mayo). ¿Qué es el malware? Definición y cómo saber si está infectado. Recuperado 22 de abril de 2022, de https://es.malwarebytes.com/malware/
Panda Security (s. f.). Hoaxes: bulos y falsas alarmas en Internet. Panda Security. Consultado el 12 de mayo de 2022. https://www.pandasecurity.com/es/security-info/hoax/
BIOGRAPHIES
Edgar Javier Palacios Zamora student from the Francisco Gavidia University of San Salvador, from the faculty of Economics and from the Bachelors of Corporative Communication, lover of singing music and empirical musician, I love reading and learning is my passion. I have a diploma in speech and news presentation by COMSAL Salvadoran communicators, a diploma in mobile app creation, a diploma in digital marketing, advanced English and basic Portuguese. Knowledge is power and power is in our hands when we use it to create peace.



